[ad_1]
Having an always-listening device in your home is a pretty common occurrence nowadays, particularly with the proliferation of Amazon’s Echo line of devices and the Google Home series. While they’re incredibly useful pieces of technology, they’re not without their privacy concerns. They have always-active microphones and an internet connection, which for some people, is too much of an invasion of privacy for them to be in the home. Security researcher Matt Kunze has proven that those fears may well be justified, as he was able to turn his Google Home Mini into what can essentially be described as a wiretap.
While this vulnerability was discovered and tested on a Google Home Mini, Kunze says that he assumes the attack worked similarly on other smart speaker models from Google.
Reverse engineering the Google Home Mini
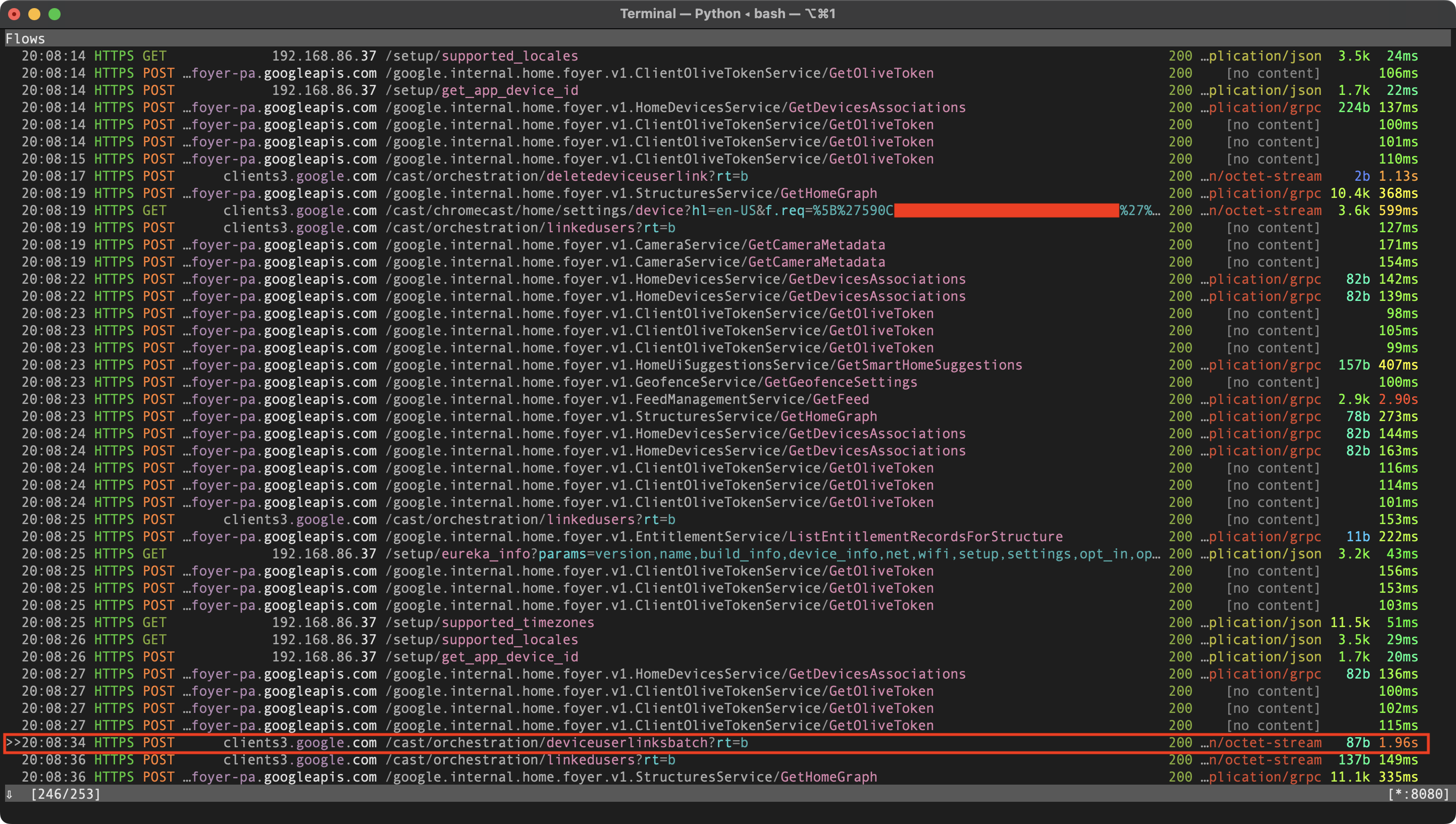
A POST request to a /deviceuserlinksbatch endpoint, as identified via mitmproxy.
Linking an account to a Google Home device gives you a lot of control over it, with the device’s “Routines” being able to execute commands remotely. Routines are useful for pre-defining functionality based on specific conditions, but they can be abused if one is able to access the device remotely and control it. An example of a routine would be to say “Hey Google, good morning”, and it turns on your lights and tells you the weather for the day.
Kunze set out to discover if it was possible for an attacker to link their own Google account to someone’s Google Home. This would essentially allow him to leverage the control given by linking an account to a device, and be used to execute commands remotely on someone’s network.
Making use of tools such as man-in-the-middle proxy (mitmproxy) and Frida, he was able to observe traffic between the Google Home application on a smartphone and the Google Home device. From there, he discovered that you could link a Google account to the device by getting its information through a local API, and then sending a request to Google’s servers with information to link it. Kunze wrote a Python script that takes Google credentials and an IP address and then links the Google account to the device at the given IP address.
Once he had control over the given device, he could create any routine and activate it on a linked device. You can invoke the Assistant to call a phone number, which he was able to do at any time. To make the attack as stealthy as possible, Kunze also enabled “night mode”, which decreases the maximum volume and LED brightness. Music volume is entirely unaffected, which makes it less likely for the user to notice.
However, it gets worse, as you don’t even need to be on the same Wi-Fi network for this attack to work: you just need proximity to the device. If you send deauthentication packets to a Google Home device, it thinks that the network has gone down and creates a Wi-Fi network so that you can connect to it again and reconfigure it for a new Wi-Fi network. Deauthentication frames (which are a type of management frame) can be sent by sniffing the IP address and is hard to protect against, as WPA2 networks don’t encrypt management frames.
However, in the same way that you can abuse the local API of the Google Home device and link it to a Google account by being on the same Wi-Fi network, you can do the same once you connect to it when it’s in set-up mode.
Remotely listening to the Google Home’s microphone
Kunze wrote and tested a detailed proof of concept of how a Google Home Mini could be used to spy on someone.
- Create an “attacker” Google account.
- Get within wireless proximity of the Google Home.
- Start sending deauthentication packets to the Google Home.
- Connect to the Google Home’s setup network.
- Execute the Python script to link the device to the attacker Google account.
- Stop sending deauthentication packets and wait for the device to connect to the internet.
- You can now execute commands on the Google Home device, including making it call your phone number.
An attacker can also make the device send arbitrary HTTP requests within the owner’s network. This increases the attack surface as an attacker could try to interface with other devices on the network, including the router.
Google has fixed the problem
On the bright side, after Kunze reported this on the 8th of January in 2021, Google did eventually fix it. You can no longer link an account to a Google Home device without an invite from the account already linked to it, and you can’t call a phone number remotely anymore via a routine. As well, on devices with a display, the network that the device creates for configuration is protected by WPA2 and requires a password to join.
While this vulnerability is only now being disclosed, it’s not impossible that someone else discovered these and abused it themselves. If you’re worried about always-listening devices, then this is certainly a justification for that. Even if this particular problem is fixed, that’s not to say that there won’t be more vulnerabilities in the future.
Source: Matt Kunze
[ad_2]