[ad_1]
An ongoing analysis into an up-and-coming cryptocurrency mining botnet known as KmsdBot has led to it being accidentally taken down.
KmsdBot, as christened by the Akamai Security Intelligence Response Team (SIRT), came to light mid-November 2022 for its ability to brute-force systems with weak SSH credentials.
The botnet strikes both Windows and Linux devices spanning a wide range of microarchitectures with the primary goal of deploying mining software and corralling the compromised hosts into a DDoS bot.
Some of the major targets included gaming firms, technology companies, and luxury car manufacturers.
Akamai researcher Larry W. Cashdollar, in a new update, explained how commands sent to the bot to understand its functionality in a controlled environment inadvertently neutralized the malware.
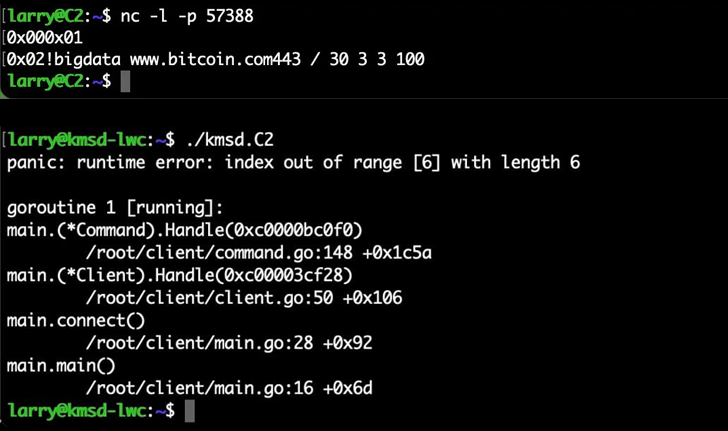
“Interestingly, after one single improperly formatted command, the bot stopped sending commands,” Cashdollar said. “It’s not every day you come across a botnet that the threat actors themselves crash their own handiwork.”
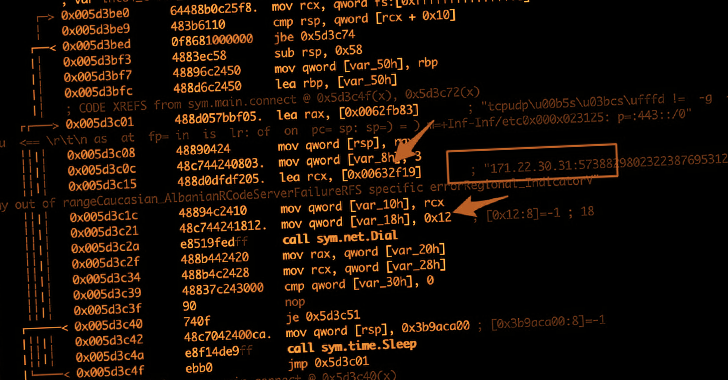
This, in turn, was made possible due to the lack of an error-checking mechanism built into the source code to validate the received commands.
Specifically, an instruction issued without a space between the target website and the port caused the entire Go binary running on the infected machine to crash and stop interacting with its command-and-control server, effectively killing the botnet.
The fact that KmsdBot doesn’t have a persistence mechanism also means that the malware operator will have to re-infect the machines again and re-build the infrastructure from scratch.
“This botnet has been going after some very large luxury brands and gaming companies, and yet, with one failed command it cannot continue,” Cashdollar concluded. “This is a strong example of the fickle nature of technology and how even the exploiter can be exploited by it.”
[ad_2]